Intrusion Detection
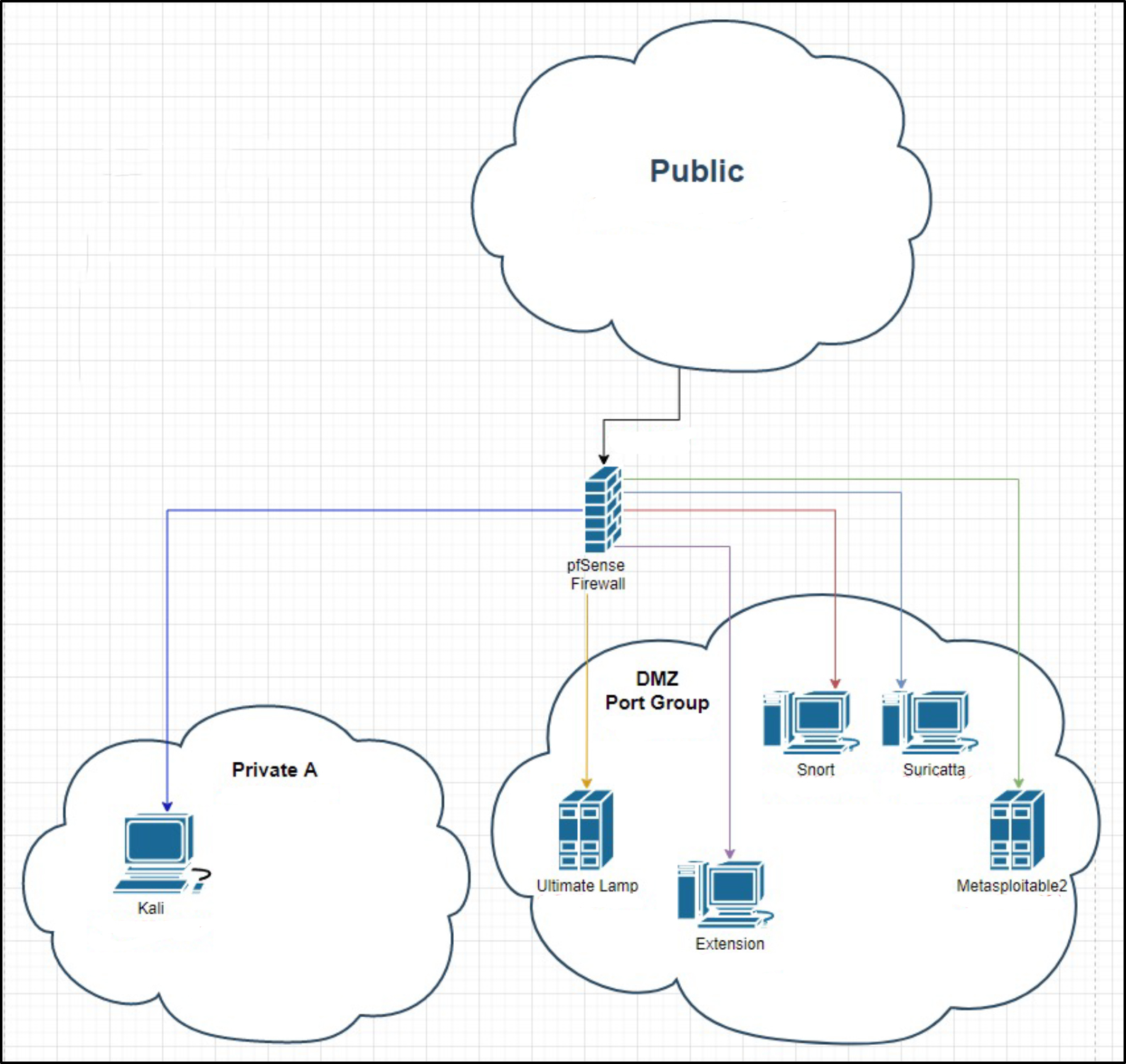
This lab is expanding upon the firewalls and VPNs labs. Network diagram can be seen below. This lab only needed the pfSense side of the lab enviorement. The lab enviorement was configured on a VMware vSphere server.
The firewall was also connected to a private network containing a simulated attacker using a Kali Linux machine. Ultimate LAMP and Metasploitable were properly configured to host services such as HTTP in order to show available ports on a port scan run by the Kali Linux attacker.
Next, Snort and Suricata were both properly configured using a Security Onion build to serve as intrusion detection systems monitoring the DMZ. An additional Snort system was configured in inline mode to serve as an intrusion prevention machine to catch and filter all traffic. These systems were all updated with the latest rule sets from a public internet database.
Finally, a Kali Linux machine was properly configured to use both Nessus and Metasploit to discover and exploit vulnerabilities on the two honeypot machines. Nessus was configured to properly generate reports on the machines about available services and related vulnerabilities. Metasploit was updated with a repository of exploits and was configured to target the two honeypot machines.
OS: Kali Linux, SecurityOnion, Metasploitable
Tools: Metasploit, Nessus, Snort IDS, Snort IPS, Suricata IDS